Pentesting in AWS
AWS is one of the top cloud service providers in the world. The company’s cloud-based platforms and web services are used by software developers, IT
professionals, and organizations of varying sizes to run various applications. This is a brief introduction to pentesting AWS cloud infrastructure.
Building a cloud-based business or moving your information assets to the cloud makes a lot of sense from an operational and cost-effective perspective. Most
third-party programs or plugins you use might also be cloud-based.
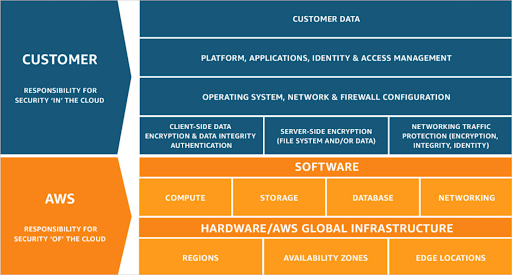
AWS like the other Cloud Providers follow the Shared responsibility model:
Organizations are still responsible for the Security “in the cloud”, meaning that the protection of the applications and data deployed in the cloud are under their complete responsibility. Consequently, we will discuss Pentesting in AWS and how the pentesting is helping companies to protect and secure their data and achieve compliance.
What exactly is Pentesting in AWS?
A team of knowledgeable penetration testers (also called “Ethical Hackers”) examines applications deployed in AWS infrastructure during a typical AWS penetration test to look for potential security holes that malicious hackers could misuse. Following the pentest, a thorough report detailing the weak points and the steps to address them is provided. The reports are following the OWASP Top 10 methodology, which is concentrating on the most common holes present in web applications or API.
Due to the Shared Responsibility Model, AWS is ensuring its part of the security (such as providing secure physical controls, patching the hypervisor, ensuring redundancy based on the SLA’s of the subscribed services,..). There are primarily four major areas to concentrate on:
- Your AWS cloud application(s) that you are hosting or developing on your platform’s external infrastructure
- Your AWS cloud’s internal infrastructure AWS configuration
- Review of AWS settings, using the AWS Well Architecture Framework
We’ve already established that the methodology and approach used in Pentesting in AWS are different from those used in traditional pentesting.
You have complete control over a traditional pentest for your own web application. As a result, the internal and external architecture of the AWS cloud, identity and access control, and AWS configuration and permissions become deciding considerations regarding AWS penetration testing.
A list of AWS controls that need to pass security tests:

The list of Amazon Web Services controls that can and must be security evaluated is provided below. It involves testing the governance body, including asset monitoring, network management, and access policies.
1. Administration:
- Define AWS borders and assets
- Access Regulations
- Identify, examine, and assess risks
- Enhance risk assessment using AWS
- IT security and program management
2 . Network Administration
- Security measures for networks
- Network ACL
- Network Security Groups
- DDoS layered protection
3. Control of Encryption
- Encryption in motion
- Encryption at rest
- Encryption in sue
- Remote access and company network extension such as AWS Direct Connect
- SSL Key Administration, certificates and PKI
4. Monitoring and Logging
- Centralized log archiving
- Review the “adequacy” of policies.
- Review the credentials report for Identity and Access Management (IAM).
- Detection and reaction to intrusions – integration with a company SIEM/SOC
AWS Testing Instruments
You may also use vulnerability scanning or cloud conformity tools integrated in AWS. In addition, there are various toolkits available to do multiple tests. Here are a few examples:
AWS Inspector: Through instant scanning AWS workloads for software vulnerabilities and exposure, this AWS tool aids in the automation of vulnerability management.
The AWS Security Hub is a tool created by AWS to centralize security warnings and automate security inspections on the platform. All accounts and regions’ security posture management is a concern.
Prowler: It’s an open-source security testing tool that lets you scan your AWS account for potential vulnerabilities, IAM permissions, and compliance using a set of standard benchmarks like the AWS Foundations Benchmark.
CloudSploit: It is a cloud security auditing and monitoring tool that allows you to audit the configuration state of your AWS account’s services. It looks for publicly accessible servers, unencrypted data storage, a lack of least-privilege policies, incorrect backup, restore settings, data exposure, and privilege escalation.
Cloudsplaining: It is an open-source AWS IAM security assessment tool that allows you to identify most minor privilege violations and generate a
risk-prioritized report for evaluation.
How to perform Pentesting in AWS?

Penetration testing, also known as pen testing or ethical hacking, tests a computer system, network, or web application to find vulnerabilities that malicious actors could exploit. AWS offers a comprehensive set of tools and services to help secure your applications and infrastructure. Still, it’s crucial also to perform regular penetration tests to identify any potential weaknesses.
Prerequisites
Before conducting a Pentesting in AWS, define the following aspects:
- The penetration test’s scope includes the target system.
- The type of test to be carried out.
- Test requirements should be agreed upon by stakeholders and the penetration testing contractor.
- A plan for the penetration test.
- A procedure that a penetration tester should follow if they discover an existing security breach.
- System owners must provide written authorization for penetration testers to conduct the test.
Identity and Access Management Testing (IAM)
When testing IAM and identity security in AWS, penetration testers should keep the following points in mind:
- Trying to see if keys exist in the root account
- Checking to see if two-factor authentication is in place
- Determining whether the root account is used for daily tasks or automation
- Checking to see if service accounts have unrestricted access.
- Inspecting to see if users have more than one key
- Checking to see if the SSH and PGP keys have not been refreshed
- Examining inactive accounts
Logical Access Control Testing
Testers should concentrate on:
- Determining whether actions have been adequately assigned to resources
- Testing whether AWS access to sensitive resources and processes is adequately controlled.
- Validating that AWS account credentials are safe and secure
Buckets S3
Testers should concentrate on:
- Ensure that relevant security features such as authentication, encryption, and so on are enabled on buckets.
- Testing buckets for security auditing—versioning, logging, and so on.
- Testing if permissions for operations like getting, PUT, and DELETE are restricted to specific users.
Database Service
Testers should concentrate on the following:
- Testing to see if data is backed up regularly and if backups can be safely restored.
- Check if sensitive resources are distributed across multiple availability zones (multi-AZ).
- Checking to see if database access is restricted to known IP addresses.
Conclusion
Finally, we proved how to conduct a Pentesting in AWS across various components of the Amazon infrastructure, including Identity and Access Management (IAM), logical access control, S3 buckets, and database services. Testers should be aware of Amazon-specific risks and attack surfaces in each of these.
Contact us to get in contact with an expert and receive a quote
